Malicious Hardware
The rapidly increasing cost to design and fabricate cutting-edge semiconductor chips forces designers to trust a few third-party foundries and third-party IPs, which makes the trustworthy of hardware an open question. Trojans are found in commercial chips as reported by University of Cambridge (link to the paper).
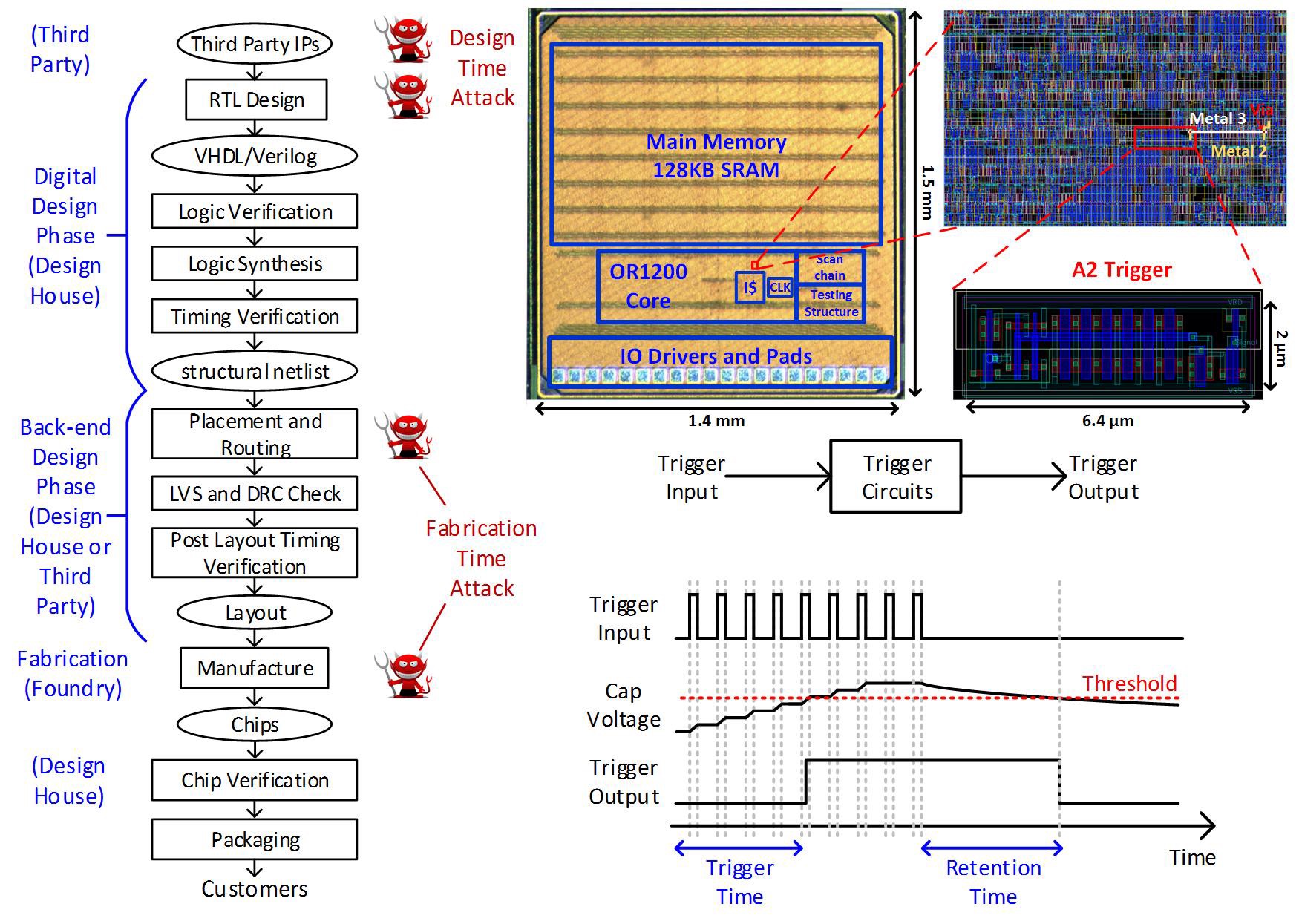
We are the first to show that an attacker can leverage analog behaviors of processors (lowest abstraction level) to insert a Trojan, which evades most existing protections based on digital behavior. The analog Trojan can be extremely small to be inserted to the final layout during fabrication time. This work was not only the first to describe such an attack, but also the first to verify it in a complete processor (open source OR1200) by 65nm silicon chips. We also demonstrated that the Trojan can be used for powerful privilege escalation.
Related Publication:
S&P16 (Oakland)