Hardware-Enabled Security Primitives
Internet of Things (IoT) are expected to bring unprecedented impacts to many industrial sectors and people’s daily lives, creating trillion-dollar economic impacts. Most IoT applications (e.g. smart home/car/factory/city) require collecting, processing, and transmitting a huge amount of private, sensitive, or safety-critical data. Security and privacy issues are widely regarded as the most critical challenges to the adoption of IoT. Securing ubiquitous devices not only face new challenges at application and network layers due to new applications, heterogeneous networks, and the huge number of devices, but also face severe constraints on computing resources, power consumption, cost, and vulnerabilities to physical and firmware attacks in edge devices. Thus, holistically designing edge devices with specialized hardware for security is of paramount importance. Typically, a minimum set of trusted hardware and software dedicated to providing fundamental security primitives for a device, named Hardware Root of Trust (HRoT), is embedded to protect device authenticity, data confidentiality and integrity, system integrity, and network availability. A full-fledged HRoT (e.g. Pluton from Microsoft and Titan from Google) consists of a random number generator, secure key management, cryptographic protocol accelerators, and a tiny host processor. Desired features of HRoT include high energy efficiency, small area, low cost, alertness and resistance to side-channel and (semi-)invasive physical attacks.
Physically Unclonable Functions (PUF):
PUFs are among the most promising security primitives for low-cost solutions of key storage, chip authentication, and supply chain protection. We work on novel physical entropy extraction methods to provide better security protection with lower power and cost overhead.
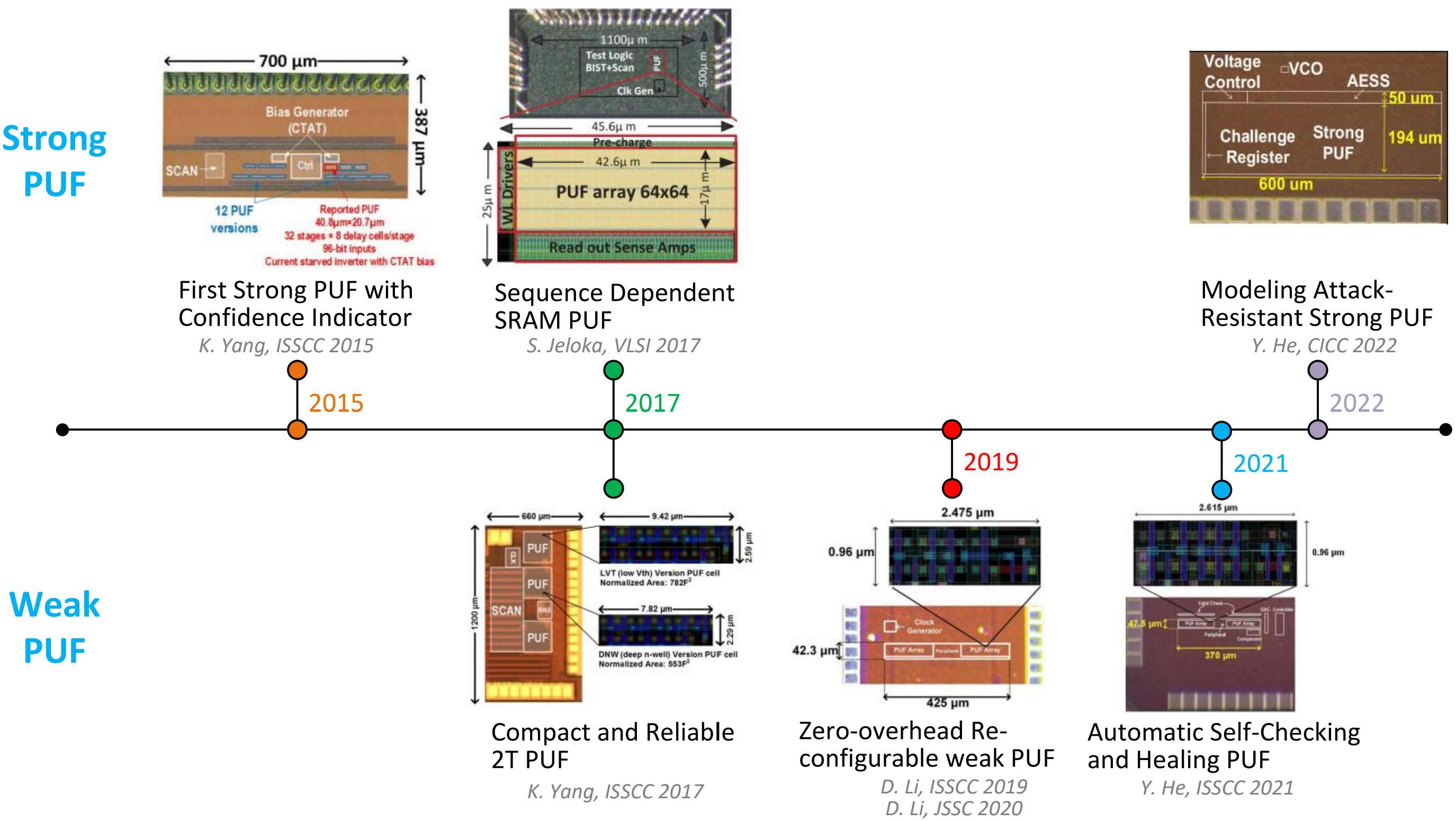
Related Publication:
CICC22
ISSCC21
JSSC20
ISSCC19
VLSI17
ISSCC17
ISSCC15
True Random Number Generator (TRNG):
Silicon TRNGs harvesting entropy from physical sources are demanded for higher security level and system integration. We work on novel TRNG designs, as well as by designing new entropy extraction concepts and circuits.
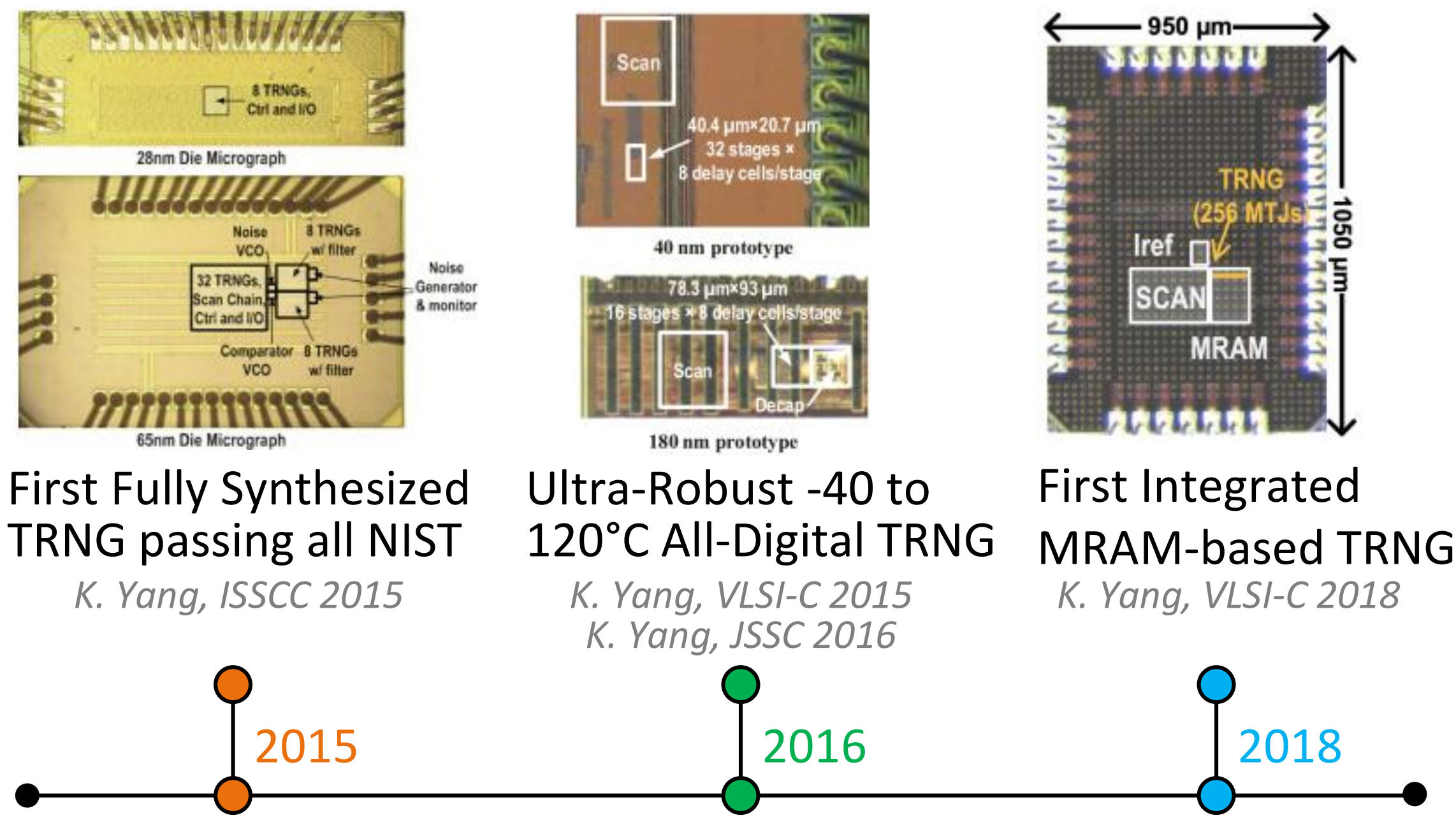
Related Publication:
VLSI18
JSSC16
VLSI15
ISSCC14
Energy-/Memory-Efficient Network Intrusion Detection:
Today’s IoT systems are plagued with security problems: as evidenced by the infamous Mirai botnet, among other high-profile incidents, these devices are susceptible to a range of adversarial attacks, many of which gain entry by remote exploits. Compared to traditional computer networks, decentralized and distributed IoT systems face new vulnerabilities raised in drastically different networks and applications, as well as computing and energy bottlenecks, especially when the exponentially increasing network traffic is considered. Network intrusion detection systems (NIDS) are highly desirable for IoT networks to monitor and react to potential attacks by detecting known attack signatures and/or anomalies in the traffic. Signature-based NIDS identifies known attacks by regular expression matching like Snort, while anomaly-based NIDS is capable of alerting new and modified attacks by finding outliers from expected network traffic models. They are complementary and provide best coverage when used together. While the computing model for the two types of NIDS are quite different, deploying them in de- centralized IoT edge and gateway devices face similar bottlenecks on energy and memory usage.
To overcome these challenges, we work on algorithm/architecture/circuit co-designs to improve the computing efficiency by 10-100 times over microcontrollers, with the ultimate goal of making these NIDS affordable in IoT sensor nodes.
Related Publication:
SSCL20